A detection system needs ongoing commitment to ensure it achieves its intended purpose, is responsive to changing and emerging risks, and is continuously improved.
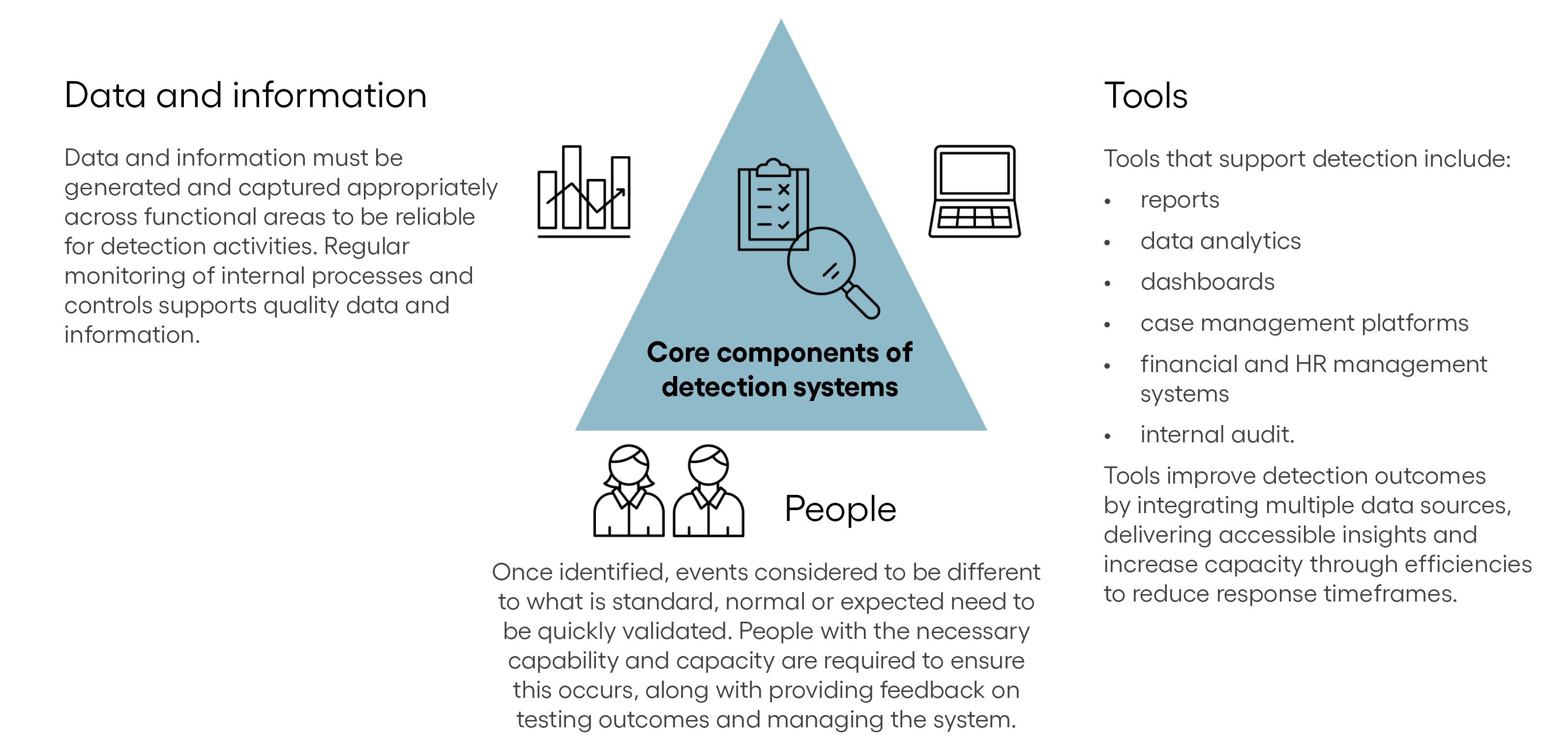
A detection system has 3 core components:
- Accurate and accessible data and information sources
- Appropriately skilled people to manage the system, validate findings and provide feedback on testing outcomes
- Tools to support testing, validation, reporting and ongoing monitoring
Data and information
Show moreInternal processes and systems generate large volumes of administrative data and information which can inform detection activities.
Using this data and information proactively can indicate if controls are working properly and if integrity breaches are occurring.
For this to be possible, an authority needs robust processes and governance to ensure relevant data and information are captured, complete, consistent and accurate.
Inadequate, inaccurate or incomplete data and information inputs, or ‘dirty’ data, mean detection outputs contain errors. ‘False positives’ might lead to unnecessary investigations or require additional investment to validate results. Integrity breaches might go unnoticed and not investigated, or investigations may be stalled. This may expose authorities to financial loss and other adverse impacts.
Governance and internal controls to protect sensitive data and information also need to be considered. Data and information should always be handled and analysed in line with privacy and data protection legislation and policy requirements.
Relevant case studies
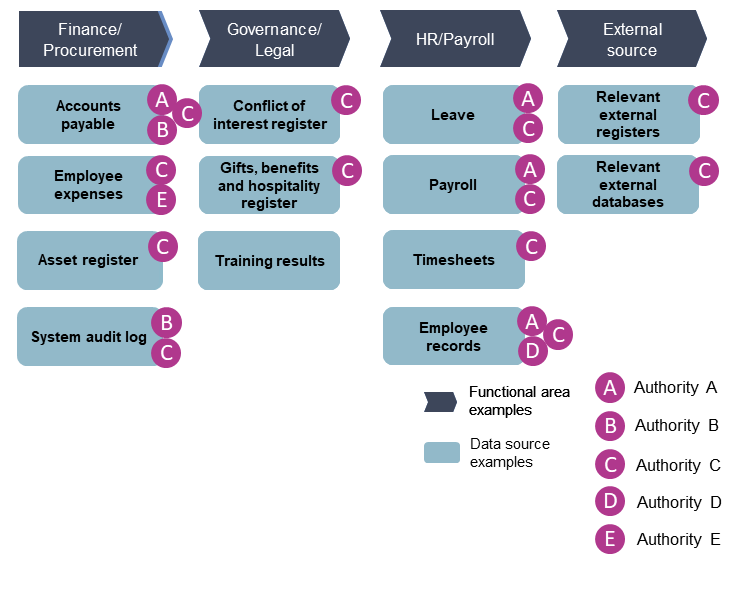
Data and information used by authorities to inform their detection systems is shown below.
Authority A identified its data sources through its internal audit plan. The plan considered functional areas with potential risks of fraud and corruption, procurement controls (such as delegations and authorisations) and other matters relevant to functional areas. The main data sources are payroll, accounts payable, revenue and procurement. The plan ensures confidentiality and restricted access are maintained over data that is sensitive or confidential.
To address potential risks in accounts payable, purchasing cards and contract management, Authority B reviewed accounts payable transactions under $50,000.
Its detection system uses data sources such as purchase orders, accounts payable, staff master records, supplier master files, purchase card transactions, system user lists, delegations of authority and supplier change logs. Access to data and information is limited to a small number of staff who can review exceptions on dashboards. Access to the virtual platform is by a secure web-based link. Passwords with secondary identification are also required.
Data and controls used by Authority C were informed by internal and external consultation and intelligence gathering, and an internal study of risks, controls and incidents. This ultimately led to sources including payroll, finance and procurement systems being used as well as over 6 external databases relevant to business processes.
Authority D implemented its detection system to reduce the risk of employing someone without finalising a criminal screening clearance, or employment occurring without a screening application. The detection system uses information from its criminal records information system, human resources system and a web service between the authority and the Australian Criminal Intelligence Commission.
Authority E implemented its detection system to identify non-compliance with finance policies and procedures. The system is informed by relevant data sources including purchasing card acquittals, purchase orders, acquittal of travel advances, travel bookings and staff reimbursements. Access to the system is restricted to key staff to ensure integrity of the reports produced.
People
Show moreWhen developing a detection system, it is important to determine if there are staff available with the right skills and experience to:
- identify events different from those considered standard, normal or expected
- undertake further investigation, validate outputs and provide feedback.
It is also important to consider the role, if any, of contractors and consultants.
Leaders set the tone from the top by supporting and approving business cases to invest in a detection system, communicating the benefits of detection to the business and championing the system’s use.
Relevant case studies
Authorities used a range of support to develop and implement detection systems such as consultants to develop the analytics, external databases and the Australian Standards.
- Two authorities reported internal support was required.
- Two authorities relied on internal and external support.
- One authority used external support only.
Tools
Show moreTools need to be fit for purpose and considered early in the development of a detection system. They can be manual or automated, with or without technology support.
Tools that support detection activities include reports, data analytics, dashboards, case management platforms, financial and HR management systems, and monitoring through internal audit.
These tools enhance detection by integrating multiple data sources, improving the delivery of insights and increasing capacity through efficiencies that reduce response times.
Relevant case studies
Data analytics support processing and testing of large volumes of data and information. Authorities B and C both use data analytics.
Data visualisation such as a dashboard can reduce the effort of manual review, enhance decision making by presenting trends and patterns, and allow for data to be better interrogated. All authorities recognise the importance of visualisations that are annotated to provide the most meaning for readers.
Case management platforms with workflows, used extensively by Authority D, can help track irregularities. They also consolidate relevant information, help to manage investigations, securely record investigation outcomes, capture root cause analysis, and help with planning and actioning remedial activities.